Pooja Choudhary
One of the reasons that individuals have been reluctant to put resources into digital money is a result of security gambles. Dissimilar to FDIC-guaranteed ledgers, cryptographic money is unregulated by most governments so you might not have lawful recourse. Although risks are associated when one uses digital wallets or makes any online transactions by marking as saving their account or card details on an external party platform, with a few cautious steps we can avoid these mistakes and save ourselves from getting hacked.
Where Are Digital Wallets Used?
Digital wallets are applications intended to take advantage of the capacities of cell phones to further develop admittance to digital items. Digital wallets basically handy to use without carrying the physical forms of money, so missing out on your pocket wallet is no more troublesome when you possess the Digi wallets.
Whenever you have your advanced wallet set up, you can utilize it to make on-the-web or contactless installments, store tickets and coupons, and a whole lot more. Apple Wallet and Google Wallet are two of the most famous ones, yet there are loads of digital wallets out there to browse.
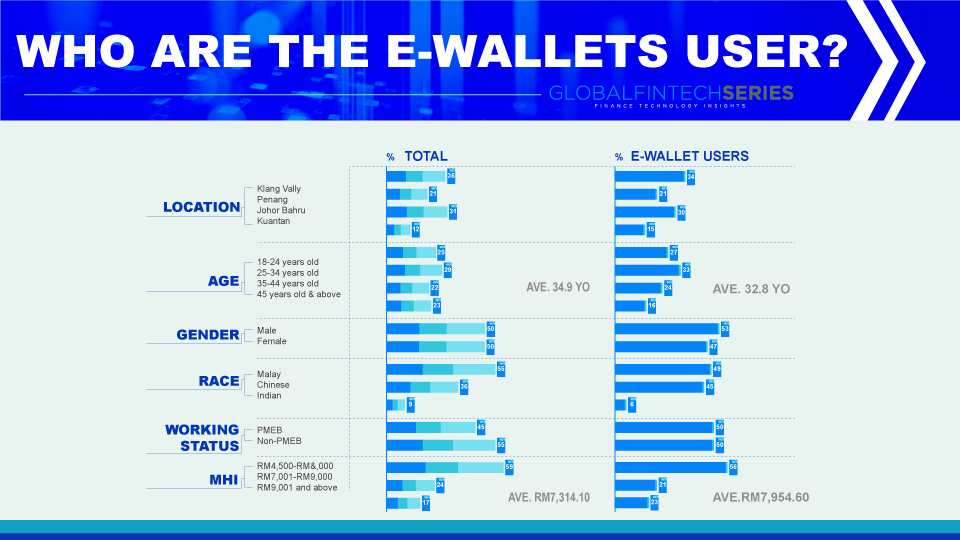
Who Are Using E-Wallets?
You don’t necessarily need a digital wallet. Nonetheless, they offer a helpful method for paying for your buys on the grounds that you don’t need to convey credit and check cards around. This additionally increments card security — you can’t lose your cards on the off chance that you don’t convey them.
Read: Did You Know- 14 Bitcoin Facts
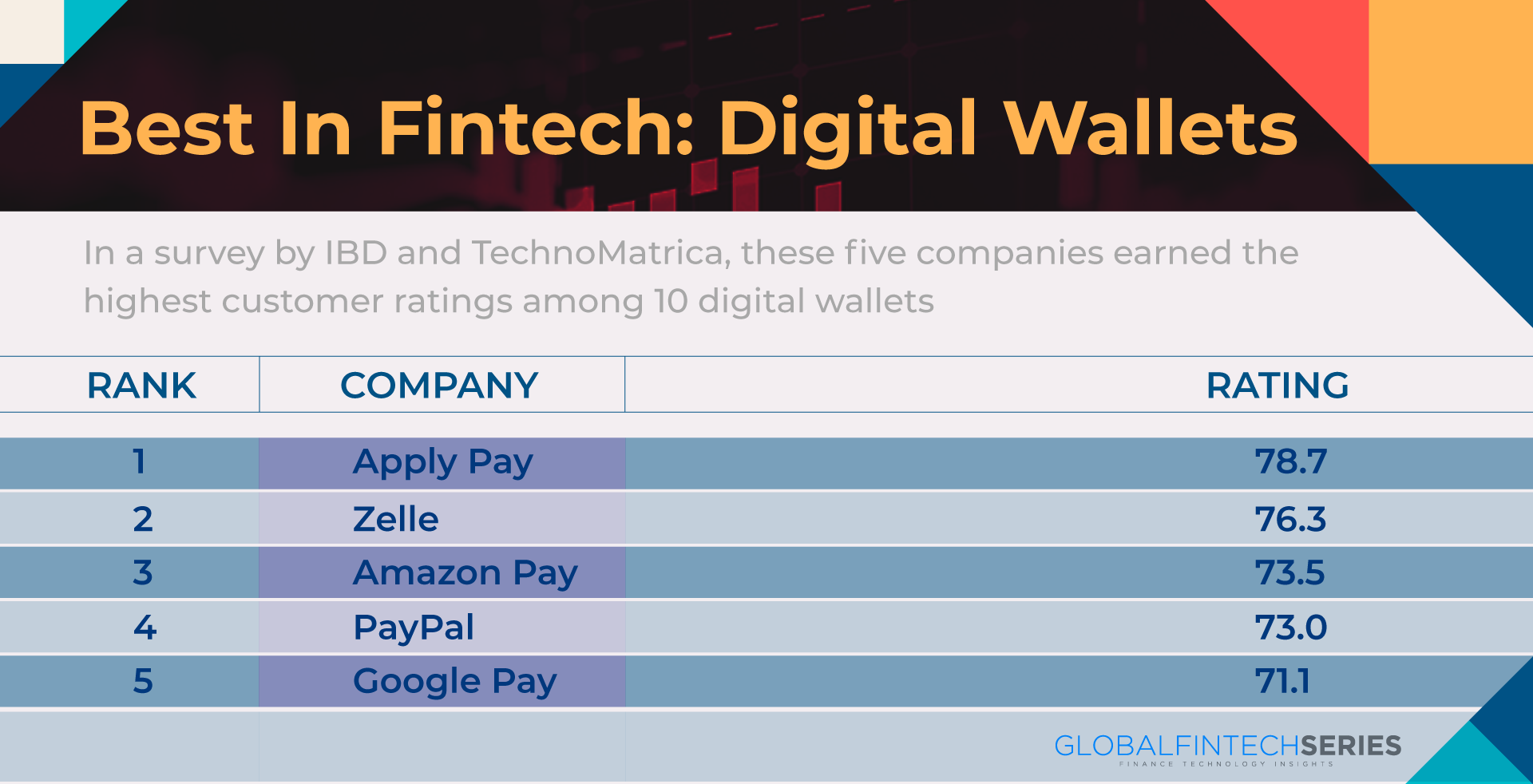
Which Company Is Heading The Run For Digi Wallets?
The Apple Pay digital app is smoothed out and accessible solely for clients of iPhones, iPads, and Mac watches. It permits clients to make exchanges for both on-the-web and in-store buys. For in-store exchanges, clients can open their telephones and hold them close to a viable retail location framework. The Apple Pay application empowers a consistent and secure method of installments, giving simplicity of involvement.
The PayPal One Touch™ application is an augmentation of the typical administrations presented by PayPal. It empowers clients to make installments or move reserves quicker by permitting them to avoid the login screen and dispense with the need to enter passwords. PayPal’s versatile wallet application can likewise be worked on a work area, PC, or tablet.
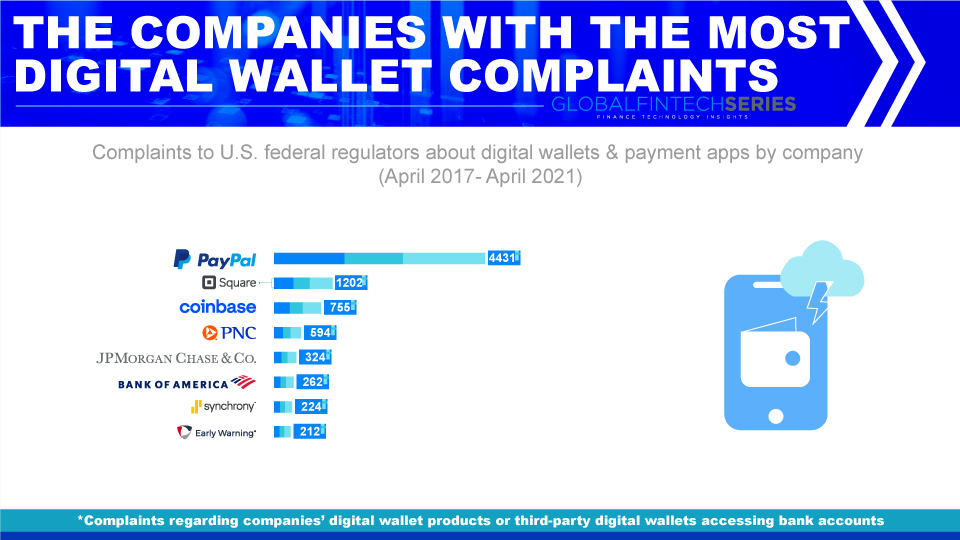
How Often Do E-wallets Get Hacked?
E-wallets are frequently eyed by hackers and out of a plethora of digital wallets the most recent worst case is for Crypto wallets. As more people invest in cryptocurrency, it increasingly becomes more lucrative for attackers. Nearly $3 billion has been stolen from crypto exchanges since 2012 and there have been about a dozen attacks since the pandemic started, with an estimated loss of over half a billion since April 2020. Hackers can steal cryptocurrency in a variety of ways, from stealing or guessing your password to hacking an exchange platform, to luring information from you in phishing attempts, and many more.
Recommended: Demystifying AR/VR Technology In Healthcare Domain
10 Ways To Keep Your Crypto Wallet Safe
Cybercriminals use sophisticated tools and techniques to hack crypto exchanges and wallets. Here are our top 10 tips on how you can secure your crypto wallets and reduce the chances of getting compromised:
1. Use A Cold Wallet
There are two types of crypto wallets that you need to understand:
Hot wallets – Wallets connected to the internet such as Exodus and MetaMask.
Cold wallets – Offline wallets, not connected to the internet, such as a USB device.
Hot wallets can be logged into from anywhere at any time, but come at a greater risk of data theft and breaches. Cold wallets require some technical knowledge to set up and are considered safer. But if you lose your offline wallet, there is no “forgot your password” option to recover it.
An excellent example is Ledger, developer of a hardware wallet with the highest possible level of security. Your crypto currency’s private keys are stored under several layers of security, in a USB stick that comes with sophisticated security measures.
2. Use 2 Factor (2fa) Authentication
2FA gives an extra layer of safety to your record. At the point when somebody attempts to sign in, you get a message or an email with a check code. This extra step makes it challenging for hackers to get to your record. They would require this check code, for which they might call and attempt to persuade you to hand it over to them. As a decent guideline, never share your 2FA code, Once Time Password (OTP), or some other secret verification code with anybody. No one from the crypto exchange calls for certifications.
3. Keep Your Seed Phrase In A Safe Place
A seed phrase is a collection of 12 to 24 random words generated by a wallet service such as MetaMask.This seed phrase must be placed in precisely the same grouping you get while marking up. Unfortunately, there is no “forgot your password” choice you can depend on. Thus, assuming you lose your seed expression, you additionally lose access to your wallet, with no exceptions. Keep this seed phrase in a safe place offline. Basically, compose it on a piece of paper and put it where you’d regularly put your things.
4. Keep A Strong Password And Change It Frequently
As per a review, 75% of millennials in the US use similar passwords across various gadgets. As surprising and absurd as it might sound, what’s the most well-known secret word? Indeed, you got it right! It’s 123456. In autonomous exploration by NordVPN, this secret phrase bested the rundown of the 200 most normally involved passwords in the world. And what amount of time does it require to break? All things considered, scarcely a second! Now envision somebody placing all their well-deserved cryptographic money in a wallet with this secret phrase. Who’s truly to blame? On the other hand, totally irregular passwords are the hardest passwords representing a serious test for programmers. Be that as it may, you likewise need to record them someplace in a protected area in the event that you can’t recall them.
5. Keep Your Investments In Multiple Wallets
Never put all your eggs in one basket. Imagine you had 2 dozen eggs. Which would be riskier? Putting all the eggs in a single basket or dividing them equally in two separate baskets? What if the basket fell? All eggs would break! But what if you had 2 baskets, and only 1 fell? The same concept applies in the world of cryptocurrency trading. Instead of putting all your NFTs and cryptocurrencies in one wallet, divide them into at least 2. Use one “hot” wallet for day-to-day transactions and a “cold” wallet for HODLing.
6. Avoid Crypto Scams On Social Media Platforms
Envision you’re watching a YouTube video on the most proficient method to bring in cash from cryptographic money exchange. The channel has more than 500,000 endorsers, and the substance maker is credible in this niche. Somewhere in the remarks, you see the station proprietor requesting that you contact them by means of their WhatsApp/Message number to contribute with them and twofold your benefits. You see the number and add it to your contacts. Without even batting an eye, you associate with them and get added to their “special” Telegram. You are currently persuaded that it is a life-changing opportunity.
Read: Invest Money Wisely In 2023 – Know The Best Ways To Invest In Cryptocurrency
Following a few days, you move $500 worth of Bitcoin, Ethereum, or some other digital currency with a commitment of “getting it multiplied to your wallet within 24 hours.”After moving the assets, you email the channel’s maker and check regardless of whether they got the assets. Unfortunately, you get an answer, “Sorry pal, which reserves? I never requested any cash.” Your whole world breakdowns. What simply occurred in this situation is one scenario of a well-known scam in the crypto world. That individual was, in all honesty, a trickster claiming to be the channel proprietor. This is going on at such an alarming rate that crypto YouTubers with a huge number of supporters are pushing YouTube to make a move on it. Whether or not YouTube truly does its part, it is time you understand that pain-free income can’t exist. This is a hazardous trick with clear warnings. However, individuals get bulldozed.
7. Stay Vigilant Of Phishing Attacks
A phishing attack is when hackers trick you into entering your user credentials into a legitimate-looking website. For instance, you might get an email from your crypto trade to quickly reset your username and secret phrase on the grounds that your account was compromised. The site looks genuine, aside from it’s anything but a real connection for that trade. Continuously guarantee that the connection is HTTPS and of the right site. Cryptographic money exchanging stage Wormhole was attacked in February 2022, which brought the loss of more than $320 million. This proceeds to show that no matter what the degree of safety, you can never depend on putting away cryptos in any web-based trade. It’s smarter to store your advanced coins in disconnected and online wallets to deal with your dangers.
8. Use A Secure Internet Connection
Working from home is a blessing. You can now turn out from a distance for organizations by partaking in your number one mug of espresso at a close by the bistro. In any case, here’s the trick: public WiFi isn’t secure and certainly impossible while making a web-based exchange from your ledger or crypto wallets. When connected with public networks, consistently use a reliable VPN.
9. Always Double-check The Recipient’s Wallet Address
A sender or receiver of cryptocurrency is identified by the wallet address. This address is a string of alphanumeric and special characters ordinarily 26 to 35 characters in length. Prior to sending the cryptographic money to another wallet, in every case twofold check the beneficiary ID. Malicious programming can alter and paste the wrong wallet address belonging to a hacker. When the exchange is made, it can never be switched on the blockchain network. Thus, it’s smarter to be protected than sorry.
10. Use Updated Antivirus Programs
Numerous antivirus programs give good protection features against crypto hacking and phishing endeavors. These programs examine all incoming emails and flag potential phishing attacks to defend your wallets. Always purchase authorized adaptations of antivirus programming and keep them refreshed with the most recent information base.
Read latest article: What Is Data Science?
Is the Future of Digital Wallets Safe Enough?
Digital wallets utilize progressed encryption to guarantee that your installment data never leaves your cell phone. Also, because advanced wallets sit inside your password-safeguarded gadget, with installments frequently just conceivable by means of unique marks, they’re very secure.
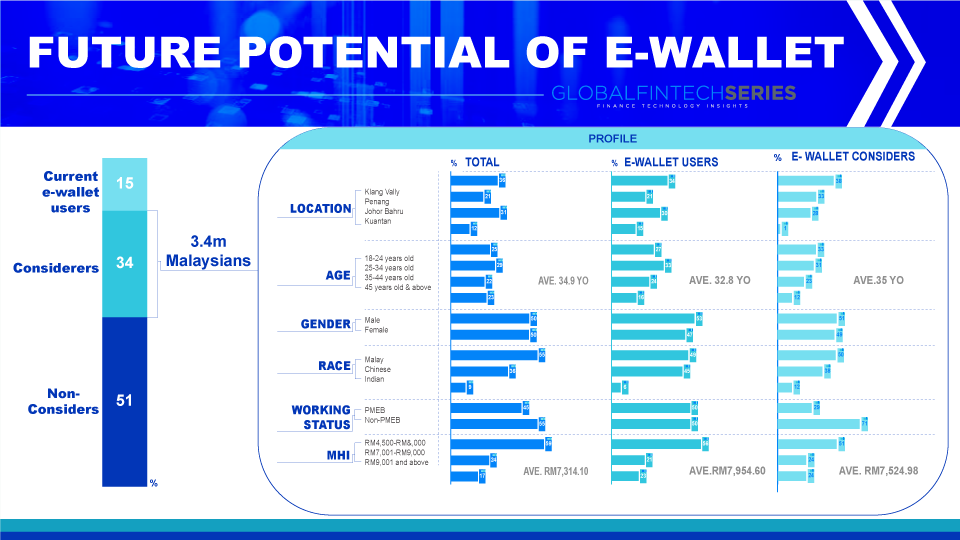
Numerous wallets additionally have extra security conventions, similar to two-factor validation one-time PINs, that can be utilized if necessary. In any case, it’s really smart to remain careful — consistently hush up about your passwords, screen your records for dubious action, and ensure that you’re ready to debilitate your gadget assuming it gets lost or taken.
Read: 5 Unconventional Ways To Make Money On Crypto In 2023